Last week I attended the RSA Conference in San Francisco, which is probably the largest yearly cyber security conference and trade show in the world with about 22,000 attendees nowadays.
One of the most popular sessions at the conference is the Cryptographers’ Panel, during which some of the founding fathers of modern cryptography discuss trends in research and cyber security in general. This year the panel consisted of Ron Rivest, Adi Shamir, Whit Diffie and Ed Georgio (former chief codemaker and chief codebreaker at NSA). During the session Adi Shamir referred to his three laws of computer security, which he formulated many years ago:
- Absolutely secure systems do not exist.
- To halve your vulnerability, you have to double your expenditure.
- Cryptography is typically bypassed, not penetrated.
The next day, I was a member of a panel about security in online and mobile banking applications, and Adi Shamir’s laws inspired me to define some laws regarding fraud in our online world prior to the panel discussion. They are as follows:
Law #1: There will always be cyber fraud
This follows from Adi Shamir’s first law, and is probably a no-brainer. We tend to work with systems that are secure enough, and try to keep fraud under control. Reducing fraud to zero would require resources that greatly exaggerate the cost of fraud itself. We try to control fraud, not remove it.
Law #2: Cyber fraud does not disappear, but is transformed (also known as the “balloon” law)
In physics, we have several fundamental laws of conservation, such as the law of conservation of energy. This law states that the total amount of energy in a closed system is constant. Energy available within the system can be transformed (e.g. from potential energy to kinetic energy), but it cannot be increased or destroyed.
I believe a similar conservation law roughly applies to fraud in our online world. Security controls that are introduced to protect online applications do not make fraud go away, but rather have criminals focus on ways to bypass these security controls or focus on other applications, i.e. they transform fraud.
The evolution of credit card fraud losses after the migration to EMV in Canada illustrates this. Prior to the introduction of the EMV standard for debit and credit cards, fraud was mainly the result of card cloning or counterfeiting. This type of fraud decreased in Canada as more and more payments card supported EMV. However, at the same time Card-Not-Present (CNP) fraud increased. Today the total amount of credit card fraud in Canada is higher than before the introduction of EMV, mainly because of the increase in CNP fraud. Similar patterns exist in other regions, such as the European Union.
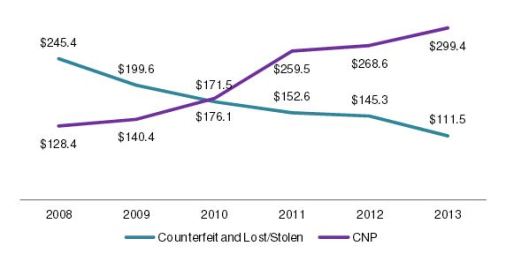
Changes in Canadian Credit Card Fraud Losses, 2008 to 2013 (In CA$ millions). Source: Canadian Bankers Association
From this perspective fraud is very much like a balloon: pressing it somewhere will make it expand somewhere else.
Law #3: Cyber fraud follows the path of least resistance
This is similar to Shamir’s third law, which stipulates that cryptographic systems are typically not broken, but bypassed. Hackers typically exploit vulnerabilities in implementations of cryptosystems and key management systems, rather than cryptanalyzing the algorithms themselves.
Again, the EMV migration in Canada illustrates this law. Because of the EMV technology, card cloning has become much harder, and certainly much harder than Card-Not-Present fraud, which involves making purchases using stolen credit card numbers. This results in higher losses due to CNP fraud.

